AWS Identity and Access Management Leveraging AWS IAM for Scalable and Secure Cloud Access Management-Ep:19
kajanan
1. Introduction
In today's cloud-driven era, securely managing access to resources is crucial for organizations of all sizes. AWS Identity and Access Management (IAM) is a cornerstone service provided by Amazon Web Services, enabling you to manage who can access your AWS resources, what actions they can perform, and under what conditions.
IAM ensures robust security by leveraging fine-grained access controls, fostering a least-privilege access model, and supporting scalable management of users, roles, and permissions. Whether you're a small startup or a large enterprise, IAM helps you protect sensitive data and maintain compliance with industry standards.
This article dives into the core components, benefits, and best practices of AWS IAM, equipping you with the knowledge to effectively secure and manage your AWS environment.
2. Key Features of AWS IAM
AWS Identity and Access Management (IAM) offers a comprehensive suite of features to ensure secure and controlled access to AWS resources. The enhancements introduced in 2024 make IAM more powerful and adaptable, addressing the complexities of modern cloud environments. Here’s an expanded view of IAM’s key features:
2.1 User and Group Management
IAM provides the ability to create and manage individual users and organize them into groups to streamline access control.
Improved Group Policy Inheritance: AWS now supports hierarchical group structures, where sub-groups can inherit policies from parent groups. This feature significantly reduces policy duplication and enhances clarity in large-scale environments.
Credential Lifecycle Management: AWS introduced automatic credential expiration and rotation reminders for individual users, improving security hygiene and compliance with best practices.
Example Use Case: A large enterprise can set up a hierarchical structure for different teams, with top-level groups defining access policies inherited by sub-groups, reducing administrative effort.
2.2 Policies
IAM policies define what actions users, groups, or roles can perform on AWS resources. These JSON documents form the backbone of IAM permissions.
Policy Validation Enhancements: The IAM Policy Simulator now includes machine-learning-driven suggestions for minimizing the use of overly permissive policies. It flags "wildcard" entries (e.g., *``) and recommends tighter access controls.
Inline Policy Explorer: AWS introduced a visual interface that allows administrators to test and debug policies in real-time, providing insights into why a policy may or may not grant specific permissions.
Example Use Case: Administrators can now use the policy explorer to validate permissions during deployment pipelines, ensuring no unauthorized access is accidentally granted.
2.3 Roles
IAM roles are essential for assigning temporary permissions to users, applications, or services.
Role Chaining Support: Enhancements now allow multi-hop role transitions across multiple AWS accounts without needing additional credentials. For example, a service in Account A can assume a role in Account B, which in turn assumes a role in Account C.
Role Session Policies: AWS added the ability to define session-specific policies, enabling fine-grained, temporary restrictions for a role's active session.
Example Use Case: A DevOps engineer automates deployment pipelines by chaining roles across accounts, enabling cross-account access while adhering to security boundaries.
d. Multi-Factor Authentication (MFA)
IAM supports MFA to provide an additional security layer by requiring users to verify their identity through a second factor.
Biometric MFA Integration: Support for biometric authentication methods like Face ID, fingerprint scanners, and voice recognition has been added, enhancing usability and security.
Adaptive MFA: AWS introduced dynamic enforcement of MFA based on contextual factors like device type, IP address, or geographic location. For example, a user logging in from a new country might be required to authenticate with MFA, even if it wasn’t enforced for their usual login.
Example Use Case: An enterprise enables biometric MFA for their development team, allowing secure and seamless access even when working remotely or traveling.
2.4 Federated Access
IAM supports federated access, enabling users to sign in to AWS using external identity providers (IdPs).
OIDC Token Management: AWS added enhanced controls for managing the lifecycle of tokens issued by OpenID Connect (OIDC) providers. Administrators can set granular expiration times and revoke tokens immediately.
Streamlined Onboarding: New APIs and pre-configured templates simplify the setup of federated users and single sign-on (SSO) integrations, reducing deployment time for large organizations.
Example Use Case: A company integrates AWS with Google Workspace, allowing employees to use their existing corporate credentials to access AWS resources securely.
2.5 Fine-Grained Permissions
IAM's support for fine-grained permissions allows administrators to define highly specific access rules.
Enhanced ABAC (Attribute-Based Access Control): Expanded conditions allow the use of runtime attributes like department names, project tags, or even user-defined variables to define access permissions dynamically.
Geographical Restrictions: AWS now allows administrators to restrict access based on precise geolocation data, ensuring compliance with local regulations.
Example Use Case: An organization restricts access to sensitive resources to employees in specific AWS regions, ensuring compliance with data residency laws.
2.6 Access Analyzer
Access Analyzer identifies unintended resource sharing and helps improve security posture.
Proactive Anomaly Detection: Access Analyzer now uses AI to detect patterns of unusual activity, such as excessive resource sharing or permissions escalation, and provides detailed alerts.
Automated Remediation: AWS integrated Access Analyzer with AWS Config, allowing one-click fixes for common misconfigurations, such as publicly accessible buckets or unintended cross-account sharing.
Example Use Case: An administrator uses Access Analyzer to identify and automatically fix a misconfigured S3 bucket that was inadvertently shared with a third-party account.
2.7 Permissions Boundaries (New for 2024)
Permissions boundaries define the maximum level of permissions an IAM entity can have.
Boundary Templates: AWS introduced predefined templates for permissions boundaries, ensuring consistent application across teams or accounts.
Boundary Conflict Resolution: New tools highlight and resolve conflicts between boundaries and explicit policies, simplifying permissions troubleshooting.
Example Use Case: A company uses permissions boundaries to ensure that developers cannot create resources exceeding the budget constraints set for their projects.
3.AWS IAM Role, Policy, User and Group, and Multi-Factor Authentication (MFA) Examples
In AWS, IAM roles, policies, users, and groups are critical components for managing access and permissions effectively. Multi-Factor Authentication (MFA) adds an extra layer of security for users. Here are examples of how to use these components together.
4.1 AWS IAM Role Example
An IAM role is an AWS identity with specific permissions that you can assume by users, services, or other AWS resources. Roles are commonly used when applications or AWS services need access to other AWS resources.
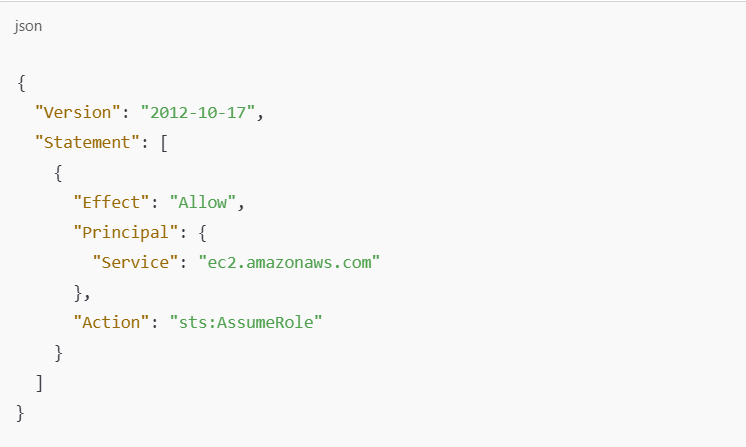
Example: Role for EC2 Instance to Access S3
This example demonstrates a role policy that grants an EC2 instance permissions to access an S3 bucket. The role will be assumed by EC2 instances.
IAM Role Policy (Trust Relationship)
The trust relationship defines who can assume this role. In this case, EC2 instances are allowed to assume the role.
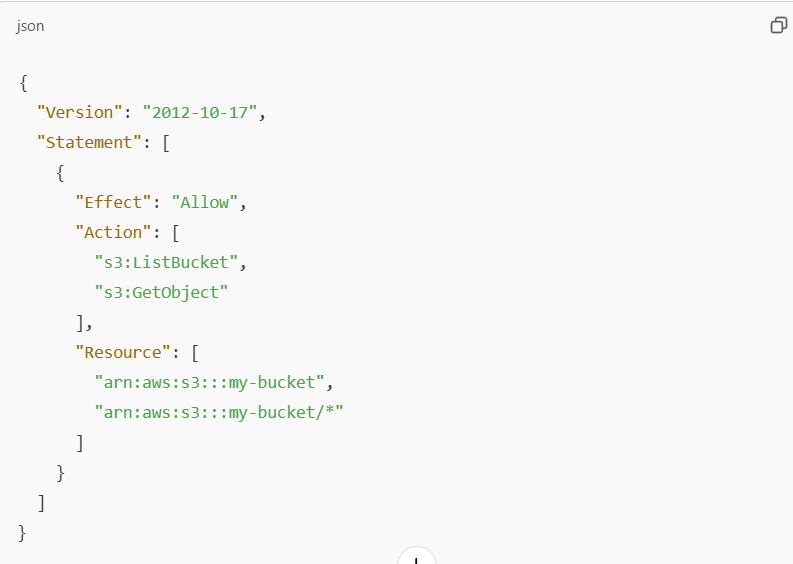
IAM Policy (Permissions)
This policy grants EC2 instances the ability to list and read objects in a specific S3 bucket
Principal: The AWS service (EC2) that can assume this role.
Action:
sts:AssumeRoleallows EC2 instances to assume this role.Effect:
Allowgrants permissions for EC2 to assume the role.
4.2 IAM Policy for User and Group
IAM users represent individuals or applications that require access to AWS resources. Groups are collections of users who share the same permissions.
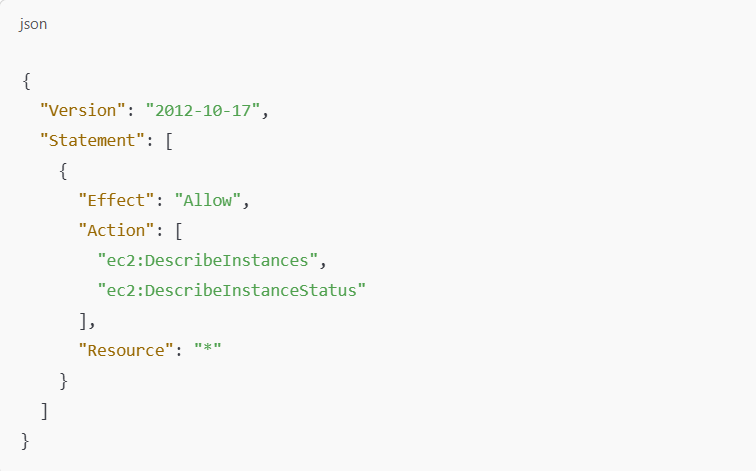
Example: Allowing Users in the DevTeam Group to Access EC2 Instances
This policy allows users in the DevTeam group to describe EC2 instances but not manage them.
Group Policy for EC2 Access
Effect:
Allowgrants permissions for users to describe EC2 instances.Action:
ec2:DescribeInstancesallows the user to view EC2 instances.Resource: `` grants access to all EC2 instances.
You would then attach this policy to the DevTeam group. Any user added to the DevTeam group will automatically inherit these permissions.
4.3 Multi-Factor Authentication (MFA) Example
MFA enhances security by requiring a second form of authentication, typically a code from a mobile device, in addition to the username and password.
Example: Enforcing MFA for IAM User Access
This example shows how to enforce MFA for an IAM user before they can access AWS resources.
Policy to Require MFA for IAM User Actions
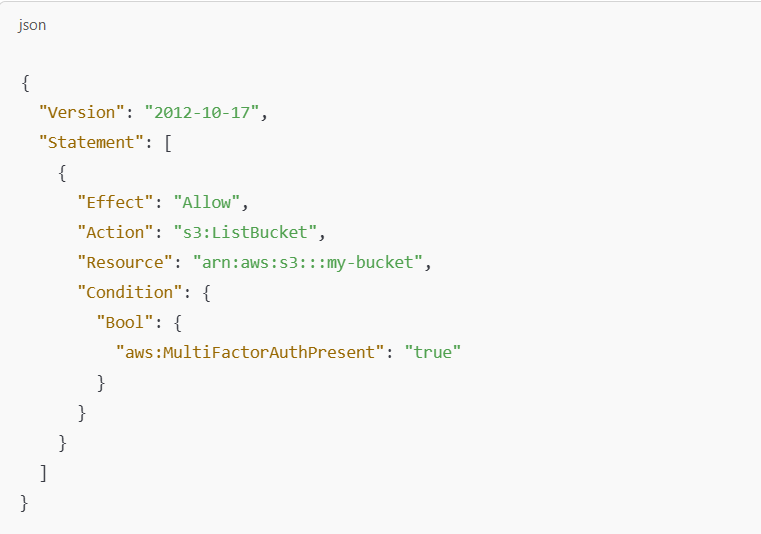
This policy ensures that actions are only allowed when the user is authenticated with MFA.
Effect:
Allowgrants permissions for thes3:ListBucketaction.Action:
s3:ListBucketallows the user to list the contents of the specified S3 bucket.Condition: The
aws:MultiFactorAuthPresentcondition ensures that the action is only allowed if MFA is present and used by the user.
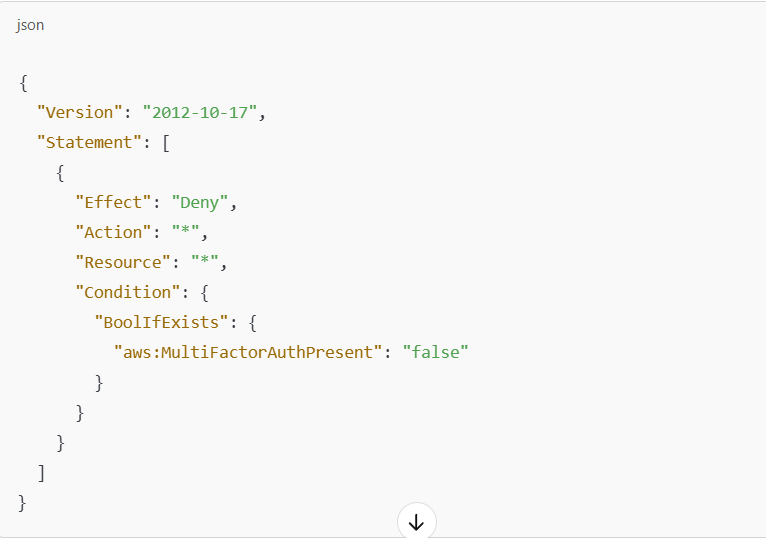
Example: MFA Enforcement for User Login (Deny All Actions Without MFA)
This policy denies all actions unless MFA is enabled for the user. It's a common practice for highly privileged users.
Effect:
Denydenies all actions (Action: *) unless the condition is met.Condition: Denies access if the
aws:MultiFactorAuthPresentcondition is false (i.e., if MFA is not enabled).
4.4 Attach MFA to an IAM User
To attach MFA to an IAM user, you can follow these steps:
Enable MFA for a User:
Go to the IAM console.
Select the user for whom you want to enable MFA.
Under the "Security credentials" tab, click on "Manage MFA device."
Follow the wizard to assign a virtual MFA device (like Google Authenticator or Authy) or a hardware MFA device.
Update User Permissions for MFA Enforcement: Once MFA is enabled, attach a policy similar to the ones above to enforce its use for specific actions.
4. Benefits of AWS IAM
AWS Identity and Access Management (IAM) provides a range of benefits that help organizations secure their cloud infrastructure, manage access efficiently, and ensure compliance. Below are some of the core benefits of using IAM, with updates reflecting the most recent improvements in 2024
4.1 Enhanced Security
Security is one of the most significant advantages of using AWS IAM, enabling organizations to secure their resources from unauthorized access.
Granular Access Control: IAM allows you to define specific permissions for each user, group, or role, ensuring that only the right individuals or services have access to the right resources.
MFA (Multi-Factor Authentication): The addition of MFA, especially with advanced options like biometric authentication and adaptive MFA (based on context), significantly reduces the likelihood of unauthorized access due to compromised credentials.
Permissions Boundaries: The introduction of permissions boundaries, which define the maximum permissions that can be granted to an entity, allows for stronger enforcement of security policies.
Example: By applying MFA and fine-grained permissions, an organization can ensure that only authorized users in specific roles (e.g., admins) have access to sensitive data, reducing the risk of a breach.
4.2 Simplified Management
IAM’s tools and features simplify the process of managing access and permissions, even for complex cloud environments.
Centralized User Management: IAM consolidates all user and group management, enabling administrators to quickly add, modify, or remove users and groups across all AWS resources.
Policy Automation and Templates: With IAM's enhanced policy validation tools, administrators can quickly generate and apply policies with less effort. Predefined policy templates also help to apply best practices for security management.
Federated Access: By integrating with external identity providers like Microsoft Active Directory or Google Workspace, IAM allows organizations to manage employee access without requiring separate AWS-specific credentials, reducing administrative overhead.
Example An enterprise using Microsoft Active Directory can integrate with IAM for single sign-on (SSO), so employees don’t need separate AWS credentials, streamlining user access management.
4.3 Cost Efficiency
AWS IAM helps organizations manage resources more cost-effectively by restricting access to only the necessary services, thus preventing misuse.
Least Privilege Principle: IAM’s fine-grained permission management ensures that users only have access to the specific resources they need, preventing unnecessary resource usage or accidental modifications that could result in cost overruns.
Policy and Role Inheritance: With the ability to assign permissions hierarchically (e.g., inherited from groups), administrators can avoid the need for redundant policies or roles, reducing complexity and minimizing the chance for mistakes.
Temporary Credentials for Roles: Using roles for temporary permissions instead of long-lived credentials means there’s less chance for credentials to be accidentally exposed or misused, reducing the overhead of credential management.
Example : An organization uses IAM roles with temporary access for contractors, ensuring they only have access to resources for the duration of their contract, thus minimizing unnecessary resource consumption.
4.4 Compliance and Auditing
IAM plays a crucial role in ensuring that organizations meet industry standards and regulatory requirements.
Audit Trails with CloudTrail: IAM works seamlessly with AWS CloudTrail, providing a detailed record of all API requests made by users and roles. This enables organizations to maintain a clear audit trail for compliance and security monitoring.
Policy Analysis and Risk Mitigation: IAM Access Analyzer helps organizations assess whether their resources are being shared unintentionally, mitigating risks that could violate compliance regulations.
Automated Remediation: IAM integrates with AWS Config to provide one-click automated fixes for common policy misconfigurations, helping organizations maintain compliance without manual intervention.
Example: A healthcare company utilizes IAM, combined with CloudTrail, to track user access to sensitive patient data, ensuring compliance with HIPAA regulations.
4.5 Scalability and Flexibility
AWS IAM is designed to scale easily with your AWS environment, making it suitable for organizations of all sizes.
Integration with AWS Services: IAM integrates with nearly all AWS services, allowing you to control access to resources at scale. As your organization grows, IAM can adapt to your evolving needs without the need for major reconfigurations.
Cross-Account Access: IAM’s support for cross-account access allows businesses to share resources securely between AWS accounts without compromising security. Features like Role Chaining enable easier management of access across multiple accounts.
Automated Role Assignments: The ability to programmatically assign roles or permissions to new services or users via IAM allows for easy integration into automation workflows, ensuring seamless scaling and minimal manual intervention.
Example Use Case: A multinational corporation can create distinct AWS accounts for each country it operates in, while using IAM roles to allow specific users and services to access resources across accounts securely.
4.6 Ease of Use
AWS IAM provides user-friendly interfaces, APIs, and tools that simplify the setup and management of access controls.
Visual Policy Tools: The IAM Policy Simulator and policy validation tools have become even more user-friendly, providing administrators with the ability to test and visualize policies before they are implemented.
Pre-configured Templates: IAM provides easy-to-use templates and wizards for setting up common access patterns (e.g., S3 access, EC2 management), reducing the complexity of policy creation for administrators.
Role-Based Access Control (RBAC): With IAM, it’s easier than ever to define and enforce role-based access policies for users and services, ensuring that users only access resources they need to perform their job functions.
Example: An administrator uses the IAM Policy Simulator to create a custom policy for an application team, testing it thoroughly to ensure no unnecessary permissions are granted before implementation.
4.7Integration with Third-Party Tools
IAM integrates well with a variety of third-party security and identity management tools.
Support for Identity Federation: IAM allows for seamless integration with popular identity providers such as Okta, OneLogin, and Active Directory, enabling Single Sign-On (SSO) and Federated Authentication, which centralizes user management and enhances security.
Automation Tools and CI/CD Integration: IAM’s APIs and SDKs allow integration with DevOps tools for automated role assignments, access controls, and permissions management within continuous integration and deployment (CI/CD) pipelines.
Example: A company integrates IAM with its CI/CD pipeline, using automated role assignments for developers based on the deployment stage, ensuring they have only the necessary permissions for each task.
5. Pricing of AWS Identity and Access Management (IAM) – 2024 Updates
AWS Identity and Access Management (IAM) remains one of the most cost-effective services in the AWS ecosystem. As of 2024, there have been some updates and clarifications in pricing details, but the core offering of IAM services continues to be free for the basic features. Here's an updated look at the pricing for IAM, taking into account the latest information:
5.1 Free Features
The following IAM features remain free:
Creating IAM Users, Groups, and Roles: The creation and management of IAM users, groups, and roles continues to incur no costs.
Permissions and Policies: Defining permissions and creating both managed and custom policies for users, groups, and roles remains free.
Multi-Factor Authentication (MFA): Enabling MFA for IAM users remains free. This includes virtual MFA apps and hardware MFA devices for additional security.
Access Analyzer: AWS Access Analyzer, which helps identify unintended resource sharing with external entities, continues to be available at no cost, making it an important tool for improving security.
Federated Access: IAM’s ability to integrate with external identity providers like Microsoft Active Directory, Okta, and Google Workspace for federated access to AWS services remains free.
CloudTrail Logging (Basic): Basic logging of IAM activity within AWS CloudTrail is still free for the first 90 days, with extended retention options available for a fee (more details below).
5.2 Costs Associated with IAM (Indirect Costs)
While IAM itself remains free, there are associated services where you may incur additional costs in 2024:
AWS CloudTrail (Extended Retention): CloudTrail logs IAM-related activity for free for the first 90 days. However, if you wish to retain logs for longer periods, you must pay for extended log storage.
Pricing: After the first 90 days, extended retention incurs a charge of $2 per GB of log data per month.
AWS SSO (Single Sign-On): AWS Single Sign-On integrates with IAM and is free for up to 50,000 monthly active users. After that threshold, additional charges apply for each active user beyond 50,000.
Pricing: As of 2024, $2 per monthly active user for users above the 50,000 limit.
API Calls and Requests: While API calls related to IAM management (such as creating/deleting users, groups, and roles) remain free, the services that interact with IAM (such as EC2 or Lambda) may have their own associated costs. For instance, if you use IAM to control access to S3 buckets, any operations on S3 storage will be billed separately.
IAM Roles for EC2 and Other AWS Services: IAM roles used in conjunction with services like EC2, Lambda, or S3 remain free in terms of their creation and management. However, the associated services (such as EC2 instance charges, Lambda execution costs, or S3 storage fees) will still apply.
5.3 New Features and Updates
In 2024, AWS made some additional updates to IAM that might influence your costs:
IAM Identity Center (formerly AWS SSO) Updates:
AWS has rebranded AWS SSO as IAM Identity Center to offer a more unified identity management experience. IAM Identity Center now includes even more integrations and broader support for third-party identity providers.
Enhanced capabilities for managing hybrid identity environments, particularly for larger enterprises. These updates continue to be free for up to 50,000 monthly active users, with costs applying only for users above that threshold.
IAM Access Analyzer Enhancements:
New features in IAM Access Analyzer include deeper integration with AWS services, such as Amazon S3 and Amazon EC2, for identifying risky resource sharing and providing more granular security insights.
No additional costs for using Access Analyzer, but its integration with services like CloudTrail for log storage could increase costs depending on your usage.
IAM for Lambda and Other Serverless Services:
There is now more emphasis on integrating IAM directly into AWS Lambda and other serverless offerings. Although using IAM to control access to serverless resources is free, the execution costs of these services (such as Lambda invocation fees) will apply.
Enhanced CloudTrail and Compliance Features:
In response to growing demand for security and compliance, AWS has introduced more advanced CloudTrail features like continuous logging for IAM events and real-time anomaly detection, which are charged based on data volume.
5.4 Summary of Key Costs
Free Features: IAM user creation, role and policy management, MFA, Access Analyzer, federated access, and basic CloudTrail logs (first 90 days).
Additional Costs:
Extended CloudTrail log retention: $2 per GB of log data per month.
AWS SSO (IAM Identity Center) beyond 50,000 monthly active users: $2 per user/month.
Costs for interacting services (e.g., EC2, Lambda, S3) still apply based on usage.
6. Use Cases for AWS Identity and Access Management (IAM)
AWS Identity and Access Management (IAM) continues to be an essential tool for managing access control and ensuring the security of cloud resources. As of 2024, IAM has evolved to address more complex requirements across various industries. Here are several updated and new use cases that highlight the versatility of IAM
6.1 Fine-Grained Access Control for Hybrid Cloud Environments
In 2024, hybrid cloud strategies are more common than ever, where enterprises use both on-premises data centers and public cloud platforms like AWS. IAM allows organizations to securely extend their internal identity systems (e.g., Microsoft Active Directory, Okta, or Google Workspace) to the cloud using federated access.
A company with a hybrid infrastructure requires secure access to AWS resources for employees working both in the cloud and on-premises. By integrating IAM with existing identity providers (e.g., Azure AD), the organization can provide a seamless, secure experience for employees without requiring multiple logins, enabling access to AWS resources such as S3, EC2, and Lambda.
6.2 Securing Serverless Architectures
As serverless architectures become more popular, IAM’s role in securing these environments becomes crucial. With IAM roles for services like AWS Lambda, users can control which services a serverless function can access at runtime, reducing the attack surface.
A company develops an application using AWS Lambda to process user data and invoke other AWS services like DynamoDB and S3. IAM roles are used to grant Lambda functions the necessary permissions to access only the required resources, ensuring that Lambda functions cannot perform unauthorized actions on other AWS services.
6.3 Simplified Access Management with IAM Identity Center (formerly AWS SSO)
IAM Identity Center (formerly AWS SSO) simplifies user management by integrating with external identity providers. This feature is especially useful for organizations that need to manage access for a large number of users across multiple AWS accounts or even external services.
A multinational company with thousands of employees needs centralized identity and access management across multiple AWS accounts. With IAM Identity Center, the company can use its existing corporate directory (like Okta or Microsoft AD) for single sign-on (SSO) access to all AWS accounts, reducing overhead and improving security by consolidating user management into a single system.
6.4 Conditional Access Based on Risk Context
IAM supports fine-grained permissions that can be used to define access conditions based on a variety of parameters, such as user attributes, IP addresses, or even time of day. With these capabilities, organizations can implement conditional access rules to improve security.
A financial institution requires its employees to access critical data only from the company’s VPN or trusted IP addresses during business hours. IAM policies are configured with conditions that enforce this access control, reducing the risk of unauthorized access from potentially compromised networks or outside working hours.
6.5 Enhanced Security with Multi-Factor Authentication (MFA)
With the increase in cyber threats, organizations are adopting MFA to add an additional layer of security. IAM’s MFA feature requires users to provide a second authentication factor beyond just passwords, making it harder for attackers to gain unauthorized access.
Use Case: A healthcare provider needs to secure sensitive patient data stored in AWS. IAM is configured to enforce MFA for all users accessing critical AWS resources like S3 buckets and RDS databases, ensuring that even if a user’s password is compromised, an attacker cannot easily gain access to protected data without the second authentication factor.
6.6 Granular Access Control for Third-Party Contractors
IAM is ideal for organizations that need to grant temporary or limited access to third-party contractors, ensuring that these external users can only interact with specific AWS resources relevant to their work.
A technology company hires a third-party contractor to manage its AWS-hosted databases. The contractor is granted an IAM role with restricted permissions that only allows them to access specific database instances, without giving them access to other sensitive AWS services like EC2 or S3. The IAM role can be temporary, and the contractor’s access can be automatically revoked once their contract ends.
6.7 Centralized Management for Multi-Account AWS Environments
Many organizations use multiple AWS accounts for different departments, teams, or business units. IAM helps centralize user access management across these accounts, simplifying security governance.
An enterprise with several AWS accounts (e.g., one for development, one for production) needs to grant users access across multiple accounts. Using IAM roles and AWS Organizations, administrators can set up centralized access controls, enabling a user to assume roles across different accounts without needing separate credentials for each account.
6.8 Regulatory Compliance and Auditing
IAM is critical for organizations in regulated industries, such as finance or healthcare, where access control and auditing are essential for compliance. In 2024, new enhancements to IAM help streamline these processes.
A financial services company needs to comply with GDPR, HIPAA, and other regulatory frameworks that require strict access control and auditing of user activity. By leveraging IAM’s integration with AWS CloudTrail, the company ensures that all IAM actions are logged, and access control policies are regularly reviewed and updated. IAM’s fine-grained permission capabilities also allow the company to enforce the principle of least privilege for all employees.
6.9 Cross-Account Access for Third-Party Services
IAM enables cross-account access, which is especially useful for situations where one AWS account needs to access resources in another AWS account securely. This is common for SaaS providers or partner integrations.
A media company using AWS for video processing allows a third-party service provider to access S3 buckets containing raw video files. The company uses an IAM role to grant the service provider’s account permissions to access specific buckets, allowing the third party to process the videos while maintaining strict control over the resources.
7.Getting Started with AWS Identity and Access Management (IAM)
AWS IAM is crucial for managing access to AWS resources securely. Here’s a quick summary of the steps to get started:
Set Up an AWS Account: Create an AWS account, which automatically grants root access.
Create IAM Users and Groups: Avoid using the root account for daily tasks. Create individual users and organize them into groups, assigning them appropriate permissions.
Attach Policies and Permissions: Assign permissions to users and groups using managed or custom IAM policies to define what actions they can perform on resources.
Enable Multi-Factor Authentication (MFA): Enhance security by enabling MFA for users, especially for privileged accounts.
Set Up IAM Roles for AWS Services: Use roles to grant AWS services, applications, or users from other accounts permissions to access your resources.
Use IAM Access Analyzer: Enable this tool to identify and mitigate unintended access to resources.
Monitor and Audit Using AWS CloudTrail: Use CloudTrail to log and monitor IAM activities, providing visibility into API calls and changes within your AWS environment.
Regularly Review and Update IAM Policies: Periodically review users, groups, roles, and policies to ensure compliance with the principle of least privilege (PoLP) and to adapt to changing business needs.
8.Conclusion
AWS Identity and Access Management (IAM) is a powerful and essential service for managing access to AWS resources securely. By offering features like user and group management, policy creation, multi-factor authentication (MFA), roles, and federated access, IAM enables businesses to control who can access what resources and under what conditions. It ensures that access is granted based on the principle of least privilege, minimizing security risks.
In 2024, IAM continues to evolve with advanced tools like Access Analyzer and enhanced policy features, making it easier to manage and secure cloud infrastructure. The integration of third-party identity providers streamlines access management, and temporary credentials for services and applications provide added security.
With IAM, businesses can scale securely, enforce best practices, and ensure compliance, making it an indispensable tool for managing access in the cloud. IAM’s ongoing updates and flexibility enable organizations of all sizes to maintain a strong security posture while efficiently managing access to their AWS resources.